ADEPT Brings Improved Cybersecurity Features
Introduction
It is a well-known maxim that security is a process rather than a product (or feature.) In this article we first discuss general process requirements for cybersecurity of industrial Linux deployments with ADEPT, and then we describe security-related features recently introduced to ADEPT to better support cybersecurity requirements.
Cybersecurity Process Requirements for Industrial Linux Deployments
ADI’s ADEPT architecture embeds real-time Linux servers into industrial or laboratory environments, as components of an advanced networked Supervisory Control and Data Acquisition (SCADA) system [1]. A deployed system includes:
- The rtx Linux servers, running ADEPT’s rtxd and performing networked data acquisition and control
- networked GUI clients (Windows or Linux) running ADEPT’s ADEPT-VI to control execution of processes under rtxd as well as to display and log data collected by rtxd.
An illustration of ADEPT’s client-server architecture is shown below, for a single client, and a server running a real-time assembly under the supervision of ADI’s real-time rtx daemon, rtxd. The real-time assembly interacts with I/O devices through Linux device drivers, and potentially also with user applications through a shared memory interface.
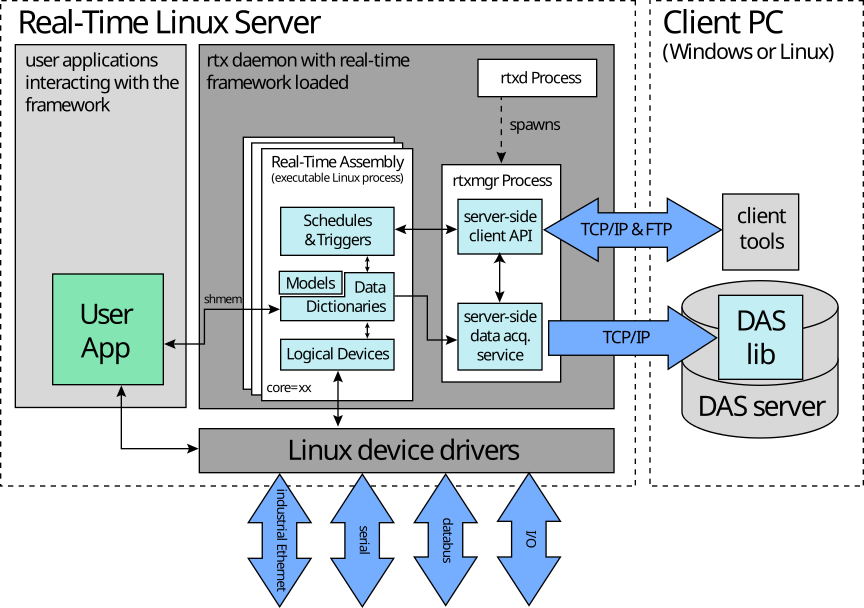
The client PC on the right of the diagram employs the ADEPT-VI (visual interface) client tool, to control the execution of the real-time assembly. Typically a client PC also hosts the development environment, ADEPT-DE, used to compile and link the assembly.
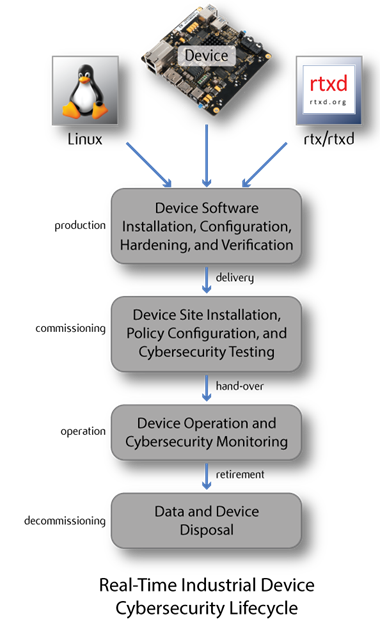
The SCADA system as a whole, including all ADEPT components, must meet operational cybersecurity requirements, including data security, throughout its lifetime. This includes the following phases, as shown in the figure below:
- design and production of the system hardware and software;
- installation, test, and commissioning of the system on-site;
- operation, monitoring and maintenance of the system, which may continue for many years;
- decommissioning of the system and disposal of its components.
A partial list of cybersecurity requirements a deployed system should meet is the following:
- enforced software development roles to ensure competent designers, coders, reviewers, and approvers;
- information segmentation so that only approved personnel have access to sensitive data, including source code and performance data;
- secure storage of archived performance data;
- prevention of physical access to the clients and servers by unauthorized personnel.
All such requirements should be considered carefully in system design and deployment.
NIST Special Publication 800-171, “Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations” [2], provides a more complete list of recommended security requirements for protecting the confidentiality of Controlled Unclassified Information (CUI), which may be used when it is not superseded by other safeguarding requirements required by law or policy.The requirements listed in NIST 800-171 fall into the following areas:
- access control
- awareness and training
- audit and accountability
- configuration management
- identification and authentication
- incident response
- maintenance
- media protection
- personnel security
- physical protection
- risk assessment
- security assessment
- system and communications protection
- system and information integrity
Cybersecurity-related features recently introduced to ADEPT
After performing an assessment of the cybersecurity requirements listed in NIST 800-171, as well as a review of customer feedback on ADEPT security features, ADI determined that provision of Active Directory ® / LDAP integration within the ADEPT client deserved the highest priority for feature development.
Initial LDAP integration was first included in the ADEPT 10.0.0.7 release [3], and makes use of the ADEPT Enterprise Server (ADEPT-ES). The figure below illustrates the architecture of LDAP integration for ADEPT client applications, as it exists in the recently announced ADEPT 10.0.9 release.
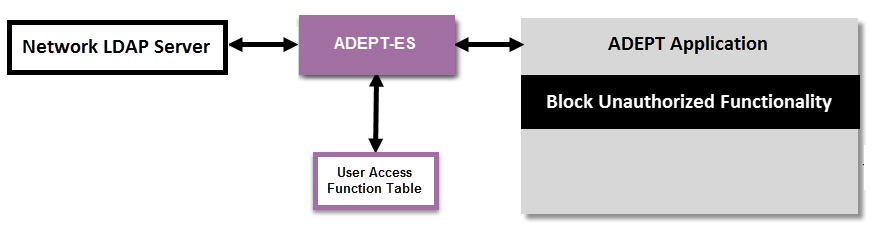
As seen in the figure, ADEPT-ES is at the center of the architecture; this is an application running on a server accessible via the client network. Among other features, it provides a central repository for control of access to ADEPT client functions by means of user group membership and user authentication. ADEPT-ES is designed to communicate with an Active Directory server on the client network, but does not itself have to reside on a Windows server – it can run as a service on Windows, or a daemon on Linux.
When ADEPT client applications are configured to use an ADEPT-ES instance on the client network, (via a configuration file with administrative permissions), the client applications require LDAP user authentication in order to access ADEPT client functions. Configuration of ADEPT-ES establishes a table of which functions are authorized for which users, based on user membership in LDAP groups. Access to unauthorized functionality will be blocked.
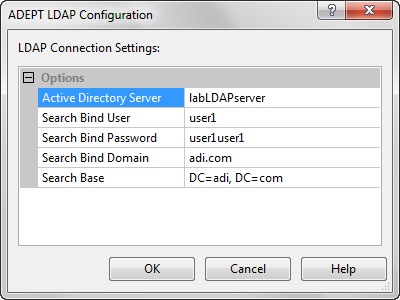
The LDAP configuration dialog box for ADEPT-ES is shown in the figure below. As shown in the figure, the server providing LDAP services must be identified, along with the domain, and LDAP user login credentials.
Once communication with the LDAP server is established, ADEPT user roles can be established by defining ADEPT role-based user groups, such as those shown in the figure below. These groups must already exist in the LDAP database.
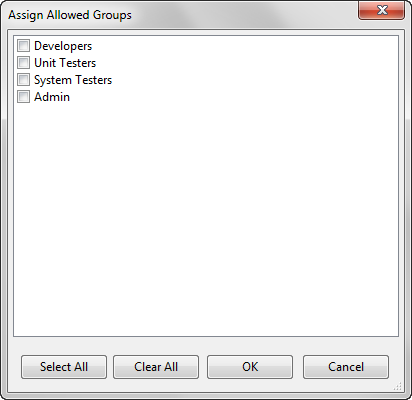
ADEPT-ES relies on standard Active Directory administration tools to create appropriate user groups and assign ADEPT users to them; it does not itself write to the LDAP database. It does, however, maintain its own table of ADEPT client application permissions as a function of group membership. This table is defined by means of the function access table GUI, as shown in the figure below.
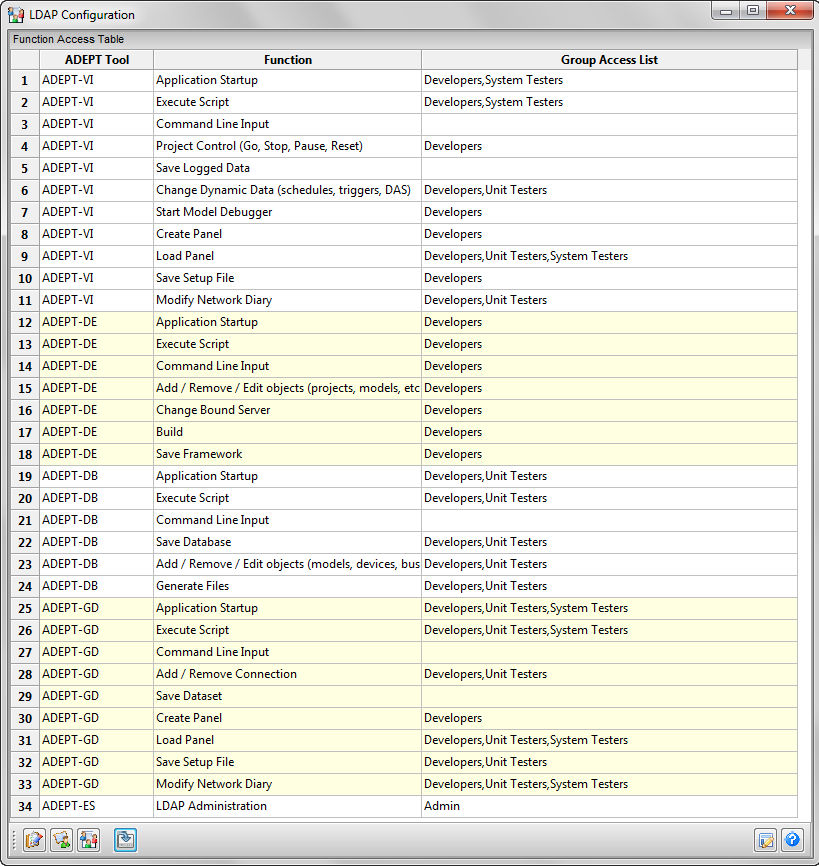
By properly defining the user groups allowed to access each ADEPT function, it could be arranged for example that personnel only belonging to the System Testers group would be able to use ADEPT-VI and ADEPT-GD functionality to execute ADEPT models (or frameworks) on ADEPT servers, but they would be unable to change the models, which would require membership in the Developers group.
The future of Cybersecurity in ADEPT Deployments
ADI is committed to developing and providing in its ADEPT architecture all features necessary for its customers to meet appropriate cybersecurity requirements for industrial Linux server deployments. The recently released LDAP support for ADEPT client applications is a significant milestone toward achieving this goal. The company is continuing to review the security requirements identified in NIST 800-171, and will develop and release additional features for ADEPT clients and rtx Linux servers based on both the standard and customer feedback.
[1] See https://en.wikipedia.org/wiki/SCADA
[2] See https://csrc.nist.gov/publications/detail/sp/800-171/rev-1/final
[3] https://techlib.adi.com/downloads/ADEPT/archive/10.0.0.7_summary.pdf
